What's more, harmonizing rules and reaction frameworks would boost coordination and collaboration endeavours. Harmonization would permit for relieve of collaboration across jurisdictions, pivotal for intervening while in the small windows of possibility to regain stolen cash.
Plan solutions ought to place additional emphasis on educating field actors around significant threats in copyright as well as the purpose of cybersecurity though also incentivizing higher security requirements.
In case you have a question or are dealing with a problem, you may want to talk to a few of our FAQs below:
Trade Bitcoin, Ethereum, and over a hundred and fifty cryptocurrencies and altcoins on the most effective copyright platform for very low costs.
On top of that, it appears that the danger actors are leveraging funds laundering-as-a-support, furnished by organized criminal offense syndicates in China and countries in the course more info of Southeast Asia. Use of this provider seeks to further obfuscate cash, reducing traceability and seemingly using a ?�flood the zone??tactic.
This tactic seeks to overwhelm compliance analysts, legislation enforcement, and blockchain analysts by carrying out thousands of transactions, both of those by way of DEXs and wallet-to-wallet transfers. Following the costly endeavours to cover the transaction trail, the final word target of this process will be to transform the money into fiat currency, or forex issued by a authorities like the US greenback or even the euro.
These threat actors were being then capable of steal AWS session tokens, the non permanent keys that enable you to request momentary credentials to the employer?�s AWS account. By hijacking active tokens, the attackers ended up able to bypass MFA controls and achieve access to Risk-free Wallet ?�s AWS account. By timing their efforts to coincide Together with the developer?�s normal operate several hours, Additionally they remained undetected right until the actual heist.}
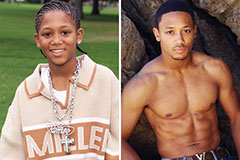 Romeo Miller Then & Now!
Romeo Miller Then & Now!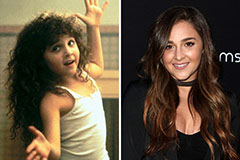 Alisan Porter Then & Now!
Alisan Porter Then & Now! Lucy Lawless Then & Now!
Lucy Lawless Then & Now! Bill Cosby Then & Now!
Bill Cosby Then & Now! Erika Eleniak Then & Now!
Erika Eleniak Then & Now!